Page 142 - Cyber Terrorism and Extremism as Threat to Critical Infrastructure Protection
P. 142
SECTION II: CYBER TERRORISM AND SECURITY IMPLICATION FOR CRITICAL INFRASTRUCTURE PROTECTION
The systems of other countries cannot be lifted wholesale and transplanted elsewhere. They
must be adapted to localized conditions, especially with regard to challenges in the security
environment, the ownership and operation of prospective critical infrastructure, the internal
administrative organization of each particular country, and the existing security institutions
and mechanisms. The topology of the foreign ownership of critical infrastructures, key assets
and key resources is also important. Each country will also require a particular roadmap for
the implementation of CIP, taking into account existing laws, institutions and resources.
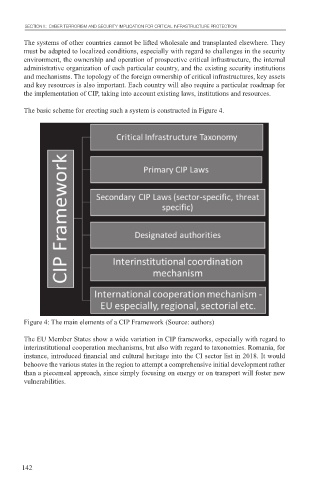
The basic scheme for erecting such a system is constructed in Figure 4.
Figure 4: The main elements of a CIP Framework (Source: authors)
The EU Member States show a wide variation in CIP frameworks, especially with regard to
interinstitutional cooperation mechanisms, but also with regard to taxonomies. Romania, for
instance, introduced financial and cultural heritage into the CI sector list in 2018. It would
behoove the various states in the region to attempt a comprehensive initial development rather
than a piecemeal approach, since simply focusing on energy or on transport will foster new
vulnerabilities.
142